🚨𝗧𝗵𝗲 𝗠𝗼𝘀𝘁 𝗘𝗳𝗳𝗲𝗰𝘁𝗶𝘃𝗲 𝗦𝗵𝗶𝗲𝗹𝗱 𝗔𝗴𝗮𝗶𝗻𝘀𝘁 𝗗𝗮𝘁𝗮 𝗕𝗿𝗲𝗮𝗰𝗵
News & Events
𝗪𝗵𝘆 𝗣𝗵𝘆𝘀𝗶𝗰𝗮𝗹 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗥𝗲𝗺𝗮𝗶𝗻𝘀 𝗘𝘀𝘀𝗲𝗻𝘁𝗶𝗮𝗹 𝘁𝗼 𝗜𝗻𝗳𝗼𝗿𝗺𝗮𝘁𝗶𝗼𝗻 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗶𝗻 𝗜𝗦𝗢 𝟮𝟳𝟬𝟬𝟭
𝗪𝗵𝘆 𝗣𝗵𝘆𝘀𝗶𝗰𝗮𝗹 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗥𝗲𝗺𝗮𝗶𝗻𝘀 𝗘𝘀𝘀𝗲𝗻𝘁𝗶𝗮𝗹 𝘁𝗼 𝗜𝗻𝗳𝗼𝗿𝗺𝗮𝘁𝗶𝗼𝗻 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗶𝗻 𝗜𝗦𝗢 𝟮𝟳𝟬𝟬𝟭
We spend so much time talking about firewalls, encryption, and phishing simulations — but what happens when someone simply walks into your server room, steals a laptop, and causes damage to company’s assets?
Why does physical security matter so much? Because many real incidents start physically:
💫 A tailgater slipping into a restricted area and accessing sensitive systems.
💫Unlocked desks leaving confidential documents visible to visitors or cleaners.
💫Natural disasters such as typhoons and flooding disrupting servers, leading to downtime or hardware damage if environmental protections aren't in place.
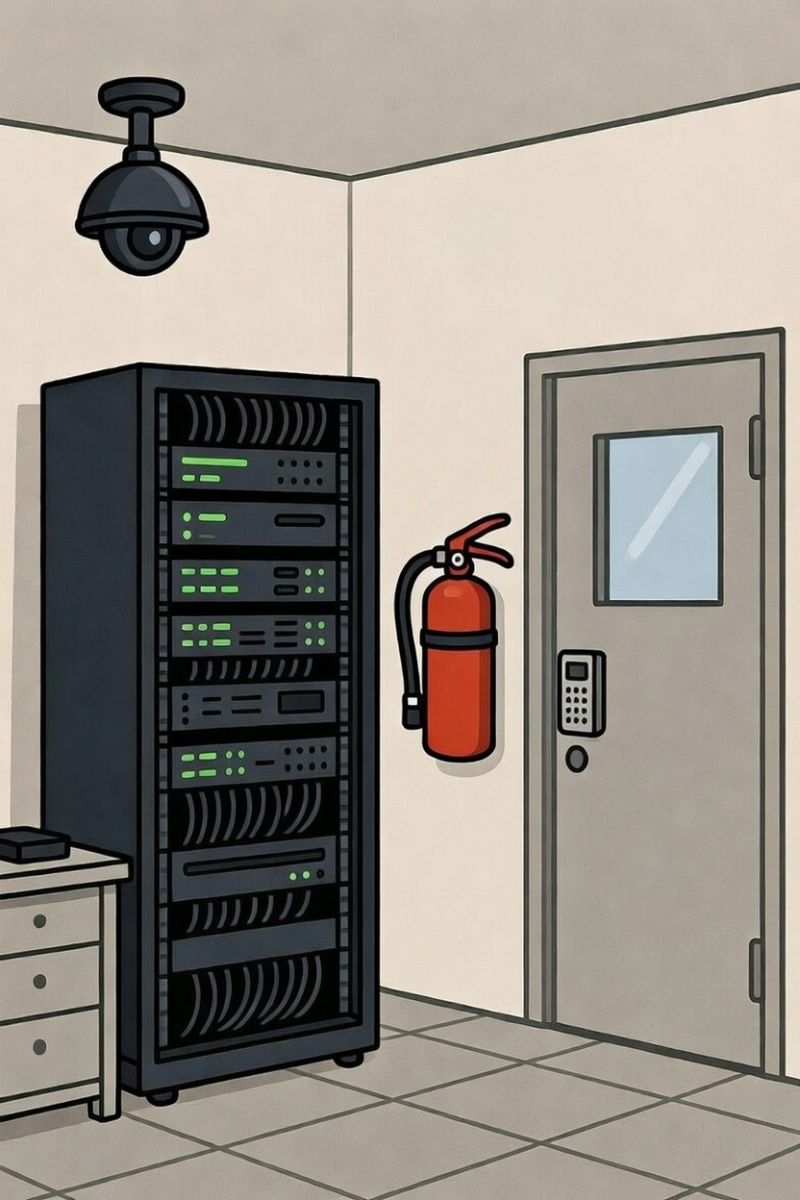
Physical security directly supports the core principles of information security—the CIA Triad (confidentiality, integrity, and availability) of data and systems. Threats such as theft, tampering, or natural disasters can bypass digital protection entirely.
In ISO 27001:2022, physical security is addressed through a dedicated theme under Annex A. Issues like expired fire extinguishers, missing CCTV footage, sticky notes with account passwords, or unlocked server room racks are common findings in an ISO 27001 audit. These are often fixed in a short time but can lead to non-conformities if ignored. Usual physical security practices are as follows:
💫 Clear desks and screens (e.g. keep sensitive information in restricted areas)
💫Physical entry and access control (e.g. door access restriction)
💫Physical Monitoring (e.g. CCTV)
💫etc.